Enabling Secure Boot in User Mode vs. Setup Mode
In this thorough article, we’ll delve into the world of secure boot and solve the puzzle of whether it should be enabled in setup mode or user mode. Secure boot is essential for guaranteeing computer system security since it guards against malware and unauthorized software. However, there exists a common issue where Secure Boot can be erroneously enabled in User Mode instead of the intended Setup Mode. This guide aims to provide a clear understanding of Secure Boot, its significance, and how to fix the problem effectively. By the time you’re done, you’ll know how to handle this situation and make sure your system is secure.
An overview of the issue is as follows: Setup Mode cannot enable Secure Boot, but User Mode may.
- Understanding Secure Boot
Secure Boot is a vital security feature that safeguards computer systems against malicious attacks and unauthorized software. We’ll explore how Secure Boot functions, its underlying mechanisms, and its role in protecting the integrity of the boot process. You may appreciate Secure Boot’s relevance and why it’s an essential part of contemporary computer systems by understanding its principles.
- Exploring User Mode and Setup Mode
To understand the issue at hand, we need to differentiate between User Mode and Setup Mode. We’ll look into the traits of each mode, their functions, and how they affect Secure Boot’s performance. You will be better prepared to deal with the issue of Secure Boot being activated in the incorrect mode if you have a thorough understanding of User Mode and Setup Mode.
- Secure Boot in User Mode
We’ll examine the specific scenario where Secure Boot is enabled in User Mode instead of Setup Mode. For an understanding of the potential risks and vulnerabilities that may emerge, it is essential to understand the ramifications of this misconfiguration. We’ll talk about potential security risks and offer information on what happens when Secure Boot is activated in User Mode.
- Secure Boot in Setup Mode
Setup Mode is intended to make it easier to configure the system, including turning on Secure Boot. We’ll examine Setup Mode’s role and goal, emphasizing how important it is to the proper working of Secure Boot. By examining the process of enabling Secure Boot in Setup Mode, you’ll gain insights into how to properly configure this security feature.
- Resolving the Issue: Fixing Secure Boot Configuration
This section will provide a step-by-step guide to rectify the issue of Secure Boot being enabled in User Mode. We’ll outline a detailed procedure to switch the system to the intended Setup Mode and correctly enable Secure Boot. With clear instructions and explanations, you’ll be able to navigate the necessary configuration changes to ensure Secure Boot is enabled as intended.
- Best Practices for Secure Boot Configuration
We’ll outline a set of best practices for Secure Boot settings to prevent errors and improve the security of your machine. These suggestions will cover a range of topics, including updating firmware, validating platform keys, and preserving system security when enabling Secure Boot. You can guarantee your system’s top performance and security by following these guidelines.
Enhancing System Security Against Malware and Unauthorized Software: Understanding Secure Boot
To safeguard computer systems from numerous risks, such as viruses and unauthorized software, Secure Boot is a crucial security component. You may improve the security of your system and protect your important data by understanding the meaning, function, and relevance of Secure Boot.
Definition and Purpose of Secure Boot
Modern computers, including those running Windows and other operating systems, all use the security feature known as Secure Boot.
Its main objective is to make sure that only reliable and digitally signed software is permitted to run at boot.
By verifying the integrity and authenticity of each component involved in system startup, Secure Boot helps prevent the execution of malicious code or unauthorized operating systems that could compromise system security.
How Secure Boot Protects Against Malware and Unauthorized Software
Malware, rootkits, and other types of malicious software that attempt to penetrate a system during bootup are deterred by Secure Boot.
It achieves this by verifying the digital signatures of various components, including the firmware, bootloader, and operating system.
Any software that lacks valid signatures or shows signs of tampering is prevented from running, ensuring that only trusted and authorized software is executed.
The Role of Secure Boot in the Boot Process
During the boot process, Secure Boot plays a crucial role in establishing a chain of trust. It verifies the integrity of each component before allowing it to execute, starting with the firmware and extending to the bootloader and operating system.
Secure Boot reduces the risk of boot kits and other sophisticated attacks that try to compromise the system early in the boot phase by maintaining the integrity of these vital components.
Importance of Secure Boot in Modern Computer Systems
In today’s digital landscape, where cyber threats continue to evolve, Secure Boot is a fundamental component of system security.
Its implementation is crucial for protecting sensitive data, preserving system integrity, and maintaining a secure computing environment.
By enabling Secure Boot, you can establish a strong foundation of trust and significantly reduce the risk of unauthorized software, malware, and boot-time attacks.
Exploring the differences between setup mode and user mode and the implications for security
In computer systems, two distinct operating modes exist Setup Mode and User Mode. Understanding the characteristics of these modes is crucial for comprehending the differences in their functionality and the security implications associated with each.
Overview of Setup Mode and User Mode
Setup Mode is primarily utilized during the initial configuration of a computer system. Users can change system settings, including boot choices, hardware configurations, and security measures, in this specialized environment.
Setup Mode is typically accessed through the system’s UEFI (Unified Extensible Firmware Interface) or BIOS (Basic Input/Output System) menu.
Contrarily, User Mode is the system’s default operating mode for normal use. The system enters User Mode, where the operating system and user applications are run after the basic system configuration is finished. User Mode offers a regulated setting that enables users to carry out their responsibilities while upholding the security and stability of the system.
Differences Between Setup Mode and User Mode
The primary distinction between Setup Mode and User Mode lies in their intended purposes and functionality. Setup Mode focuses on system configuration and customization, enabling users to define parameters such as boot order, device settings, and security options.
User Mode, on the other hand, is designed for regular system operation, providing an environment where the operating system and user applications function optimally.
Additionally, Setup Mode grants users elevated privileges to modify critical system settings, while User Mode operates with restricted privileges to ensure system integrity and security. This differentiation prevents unauthorized modifications to crucial system components during regular operation, reducing the risk of system compromise.
Security Implications of Setup Mode and User Mode
If improperly handled, the higher rights of Setup Mode could provide a security risk. Attackers may be able to get around security safeguards or install malicious software thanks to system vulnerabilities caused by unauthorized access or changes made in Setup Mode.
Therefore, it is crucial to restrict access to Setup Mode and ensure that proper authentication mechanisms are in place to prevent unauthorized changes.
User Mode, being the default operating mode, focuses on maintaining system security during regular operation. It enforces access controls and restrictions to protect critical system resources and prevent unauthorized actions.
User Mode’s inherent security measures, coupled with proper system hardening practices, contribute to a more secure computing environment.
Understanding Secure Boot in User Mode: Risks and Vulnerabilities
When the Secure Boot feature is enabled in User Mode, it poses certain risks and vulnerabilities that can compromise system security. Understanding the effects of running Secure Boot in User Mode is essential for ensuring a reliable and secure computing environment.
Current State: Secure Boot Enabled in User Mode
When the system is operating in “Secure Boot” in “User Mode,” only trustworthy and digitally signed programs are permitted to start during the boot process. There could be problems connected to this setting, though.
Impact on the Secure Boot Process
The verification procedure at system startup is impacted when Secure Boot is run in User Mode. The system may permit the execution of certain software that is signed but not explicitly trusted, even though it nevertheless confirms the integrity and validity of crucial components. This could provide malicious actors with a possible entry point to target system flaws.
Risks and Vulnerabilities
Various security hazards are introduced when Secure Boot is enabled in User Mode. Malware or unauthorized software with legitimate digital signatures can get past various security measures, endangering the stability of the system. Unauthorized access, data breaches, or the installation of malicious software that compromises the system could result from this.
Potential Attacks and Exploits
Access to several attacks and exploits is made possible by running Secure Boot in User Mode. Attackers may make use of code-signing flaws, where they acquire or create fake digital signatures to run malicious programs. They might also take advantage of flaws in reliable software parts to gain unauthorized access to or command over the system.
Additionally, since Secure Boot in User Mode might only have weak defenses against firmware-level attacks, attackers might concentrate on the firmware or bootloader. This may result in persistent malware installation and compromises that are difficult to find and get rid of.
Run Secure Boot in Setup Mode, which performs more stringent security checks and permits only trusted applications to run during boot, to lessen these risks and vulnerabilities. As a result, the system is protected from unauthorized code execution and has a greater level of security.
Understanding Secure Boot in Setup Mode: Enhancing System Security
Security and integrity of computer systems are crucially supported by Secure Boot in Setup Mode. System administrators can configure and change system parameters relating to secure boot in this mode. You can improve the overall security of your system by comprehending the function and use of Secure Boot in Setup Mode.
Setup Mode: Purpose and Function
System administrators can edit numerous UEFI firmware settings when the device is in setup mode, which is a configuration state. It offers a user-friendly interface for configuring system settings, such as secure boot options.
Operation of Secure Boot in Setup Mode
Administrators can control boot security by using Secure Boot in Setup Mode. Platform keys, which are cryptographic keys used to confirm the integrity and authenticity of firmware and operating system components during booting, can be enrolled or removed using this feature.
Importance of Enabling Secure Boot in Setup Mode
By ensuring that only trustworthy and digitally signed software is performed during the boot process, Secure Boot can be enabled in Setup Mode to increase system security. This stops the execution of unauthorized or malicious code that can jeopardize the security of the system and compromise private information.
System administrators can create a trusted boot chain by setting Secure Boot in Setup Mode and checking each component’s integrity before allowing it to operate. This provides defense against a variety of threats, including rootkits, boot kits, and other malware types that try to insert harmful code during boot.
To effectively defend the system against new threats, it is crucial to preserve the platform keys’ integrity and keep them up to date. Updating the platform keys frequently helps reduce potential vulnerabilities and ensures the system’s security posture.
Avoiding Potential Issues: Best Practices for Secure Boot Configuration
Although Secure Boot is a crucial security feature, it must be configured properly to ensure your system is fully protected.
When Secure Boot is configured incorrectly, vulnerabilities might be introduced that reduce this security mechanism’s efficacy.
You may maximize Secure Boot’s advantages by being aware of potential problems and adhering to best practices.
Common Misconfigurations and Mistakes
- Unsigned or improperly signed boot components: Firmware, bootloaders, and operating system kernels must all be digitally signed by reputable organizations for Secure Boot to function. Boot problems or security flaws might result from using unsigned or improperly signed components.
- Disabled or outdated Secure Boot: Some users may purposefully disable Secure Boot to install non-standard operating systems or get around compatibility problems. This, however, makes the machine susceptible to unauthorized code execution while it is booting.
- Unenrolled or outdated platform keys: Platform keys are used by Secure Boot to validate the legitimacy of boot components. The integrity of the boot process may be compromised by the execution of unauthorized or compromised code as a result of failing to enroll or update these keys.
Risks and Consequences of Misconfigurations
Misconfigurations in Secure Boot can have serious security implications, including:
- The boot-process execution of malware or unapproved software, which could result in data breaches, system compromise, or unauthorized access.
- The inability to recognize and stop boot kits and rootkits, can conceal harmful activity and jeopardize system integrity.
- A compromised system’s stability and dependability, frequently freezes, crashes, or behaves unexpectedly.
Best Practices for Secure Boot Configuration
To avoid potential issues and ensure Secure Boot is set up correctly, consider the following best practices:
- Use reputable hardware and firmware: Select hardware and firmware from reputable producers who regularly release security fixes and firmware updates.
- Enroll and update platform keys: Enroll platform keys frequently and update them to guarantee that only authorized code is run on boot. Take away any keys that have been compromised or are no longer needed.
- Verify digital signatures: Verify the digital signatures of boot components before installing or updating them to make sure they are authentic and unaltered.
- Enable and maintain Secure Boot: To prevent unauthorized code execution at boot, make sure Secure Boot is enabled and current. Keep an eye out for firmware changes that might enhance security.
- Educate users and administrators: Offer instruction and documentation on the value of Secure Boot and the dangers posed by incorrect settings. Encourage the use of best practices when configuring and setting up the system.
By adhering to these recommendations, you may reduce the possibility of configuration errors and guarantee that Secure Boot offers your system the desired security benefits. To address new threats and maintain a safe computing environment, be watchful, constantly evaluate, and change the safe Boot settings as necessary.
Best Practices for Secure Boot Configuration: Ensuring System Security
Maintaining system security and guarding against unauthorized code execution during the boot process depends on Secure Boot being configured correctly. You can maintain a secure computing environment and make sure Secure Boot is activated successfully in Setup Mode by adhering to best practices. This manual offers suggestions and detailed directions for configuring Secure Boot correctly.
Step-by-Step Guide for Secure Boot Configuration in Setup Mode
- Access the UEFI menu: Press the designated key (typically Del, F2, or F10) while your computer is booting up to enter the UEFI or BIOS menu.
- Navigate to Windows OS Configuration: Find the Windows OS Configuration section in the UEFI menu.
- Enable Secure Boot: Find the Secure Boot option in the Windows OS Configuration section and click “Enable.” To increase system security, this turns on Secure Boot.
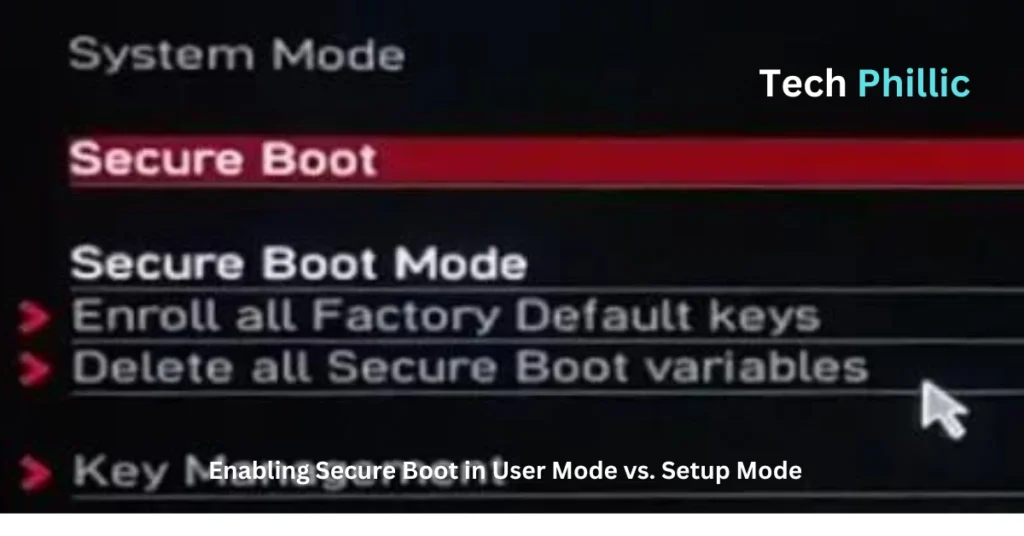
- Enroll Platform Key (PK): If you are asked to enroll the Platform Key (PK), do so by following the on-screen directions. This phase makes sure that only dependable operating systems and firmware components are permitted to run during the boot process.
- Set Secure Boot Mode to Standard: To guarantee that Secure Boot functions by commercially accepted security guidelines, set the Secure Boot Mode to “Standard”.
- Install factory defaults: Look for a factory default installation option. Choose “Yes” to return Secure Boot to its factory default configuration, assuring a safe and secure setup.
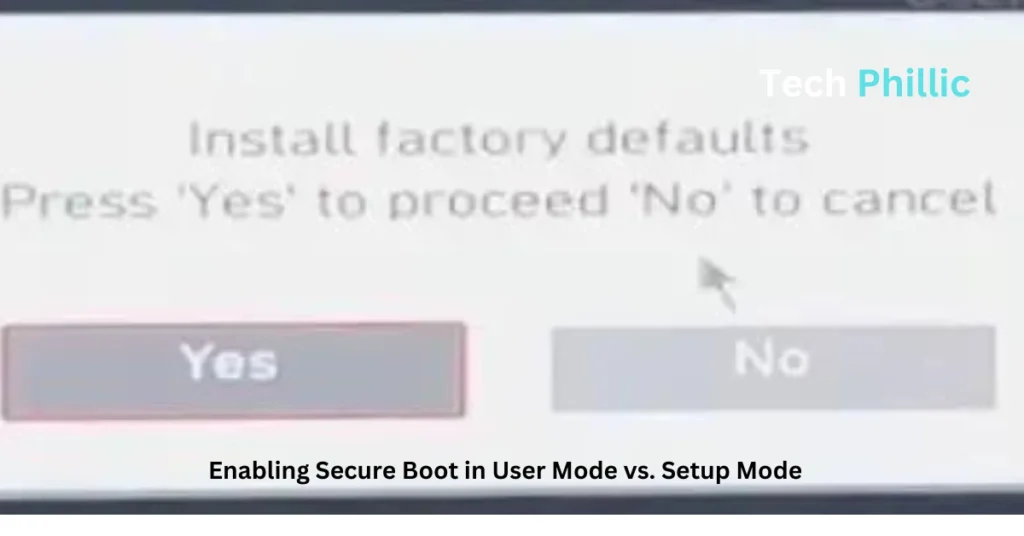
- Save and exit: Save the modifications you made before leaving the UEFI menu. To save the Secure Boot configuration, confirm the save action.
- Keep firmware up to date: Check your system’s manufacturer’s website frequently for firmware upgrades, and install them right away. Updates to firmware frequently include security fixes that fix potential flaws.
Recommendations for Maintaining System Security
- Verify digital signatures: Verify that firmware, bootloaders, and operating system components have been digitally signed by reputable organizations before installing or updating them. An extra layer of verification is offered by digital signatures to stop the execution of malicious or altered code.
- Keep operating systems up to date: Updates and patches for operating systems should be installed when they become available. Updates frequently improve system stability and fix security flaws.
- Secure the system physically: Lock your machine in a safe place and use security tools like BIOS or UEFI password protection to prevent physical access.
- Educate users on system security: Create training and awareness campaigns to inform users about the value of system security, the function of Secure Boot, and the dangers of removing or incorrectly setting it.
Considerations for Different Operating Systems and Firmware Versions
The specific menu choices and configuration settings may differ, but the techniques described above generally work with most computers. For particular instructions adapted to your operating system and firmware version, go to the documentation or support resources provided by the system maker.
By following these best practices and maintaining a secure configuration, you can maximize the effectiveness of Secure Boot and protect your system against unauthorized code execution Review and update your Secure Boot configuration regularly to address new threats and maintain system security.
ALSO READ: 15 Must-Have Chip Chick Technology and Gadgets For Women
FAQS
1. What is Secure Boot, and why is it important?
Secure Boot is a security feature implemented in modern computer systems to ensure that only trusted firmware, bootloaders, and operating system components are executed during the boot process. It helps protect against malware attacks that aim to inject unauthorized or malicious code during system startup.
2. How does Secure Boot work?
Secure Boot utilizes cryptographic keys to verify the integrity and authenticity of each component loaded during the boot process. It relies on digital signatures to validate the components against trusted certificates stored in the firmware. If a component lacks a valid signature or doesn’t match the trusted records, Secure Boot prevents its execution.
3. What is the difference between Setup Mode and User Mode?
1. Setup Mode: In Setup Mode, the system allows modifications to its firmware and security settings, including enabling or disabling Secure Boot. It is typically used during initial system setup or when making firmware changes.
2. User Mode: User Mode is the normal operational state of the system, where the firmware and security settings are locked to prevent unauthorized modifications.
4. Can Secure Boot be enabled in User Mode? What are the implications?
No, Secure Boot cannot be enabled in User Mode. The error message “System in Setup Mode! Secure Boot can be enabled when System in User Mode” indicates that the system is currently in Setup Mode, which prevents enabling Secure Boot. Operating systems and applications that rely on Secure Boot may not function properly until it is correctly configured in User Mode.
5. How do I switch between Setup Mode and User Mode?
To switch from Setup Mode to User Mode, follow these steps:
– Access the UEFI or BIOS menu during system startup.
– Navigate to the Secure Boot settings.
– Change the system mode from Setup Mode to User Mode.
– Save and exit the UEFI or BIOS menu.







